How to create a crypto wallet in 2024: A step-by-step guide
One of important step when working with cryptocurrency is to create a wallet for it. There are several main types of crypto wallets that differ in ease of use, functionality, security level and other parameters.
In this article, I reviewed the pros and cons of each type of crypto wallet, and also gave instructions on how to create them using specific services as an example. There is also a rating of the best cryptocurrency wallets of this year in the end of the article.
What is a cryptocurrency wallet?
The wallet does not store assets directly, but provides access to their address in the blockchain. This information is protected by a pair of cryptographic keys, one of which is public (visible to all network members), the second is private (the secret one).
There are different types of wallets: browser extension, desktop, mobile application and physical device.
Private keys value
First of all, let’s figure out what is the importance of private keys for assets safety and what you should wait in case of information leakage or loss of the key.
To make a transaction with cryptocurrency, the owner of the assets uses the public and private keys. The public key is the wallet address that can be shared with other users. In fact, it is same to a bank account. With the help of the public key one creates the transaction.
However, the transfer of cryptoassets requires both public key and private key. The latter is used as a CVC, so we may talk about it as a kind of wallet password.
If device with the wallet is lost, user loses access to the private key. But he can recover it with the seed phrase. This is a sequence of random words (12,18 or 24) that will help restore access to the private key and to the user’s funds. To do this, just enter the seed phrase into the wallet app on the device where it is installed.
Next, I will talk about the most common types of crypto wallets, as well as how to create them.
Desktop crypto wallets
This is a type of software (“hot”) wallets, which are presented as an application installed on a PC. Private keys are stored on the user’s computer, and only he has access to them. If you decide to install a desktop wallet, it is important to take extra security measures, such as enable two-factor authentication and use an antivirus.
Desktop wallet guide
Let’s consider how to get a desktop wallet using Exodus as an example. Check the instruction below:
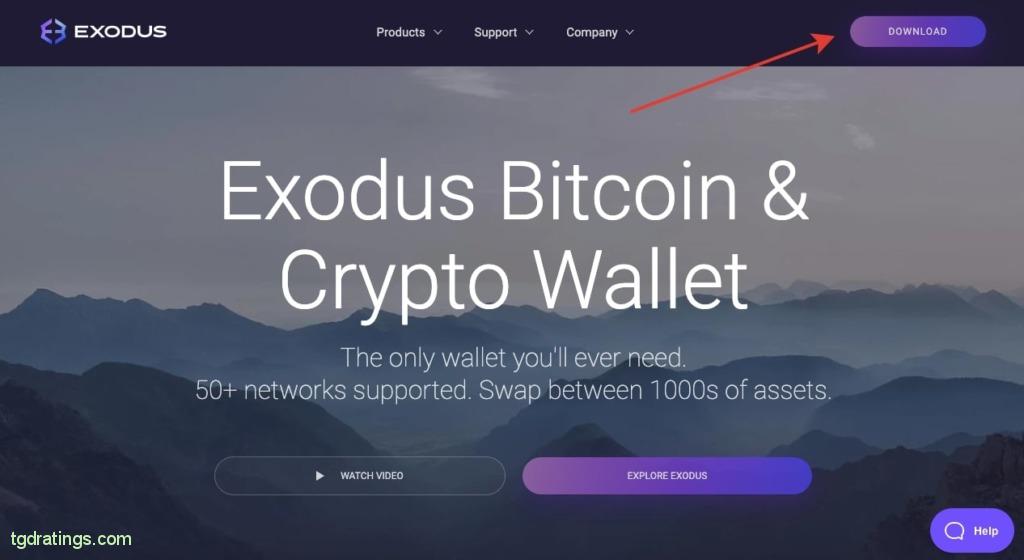
- Click Download in the upper right corner of the official wallet’s website;
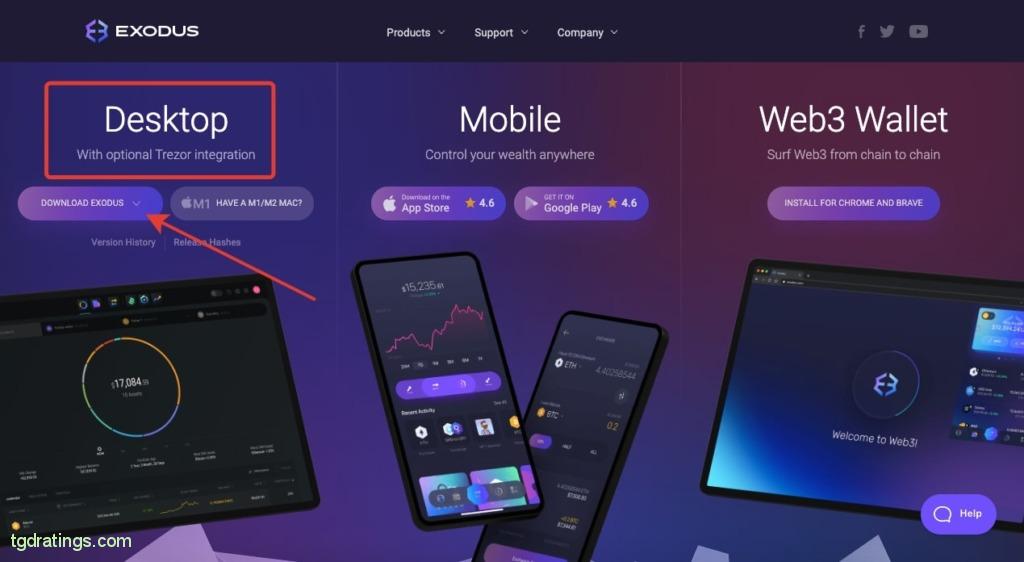
Exodus download - Select Desktop from the suggested wallet types → Download Exodus;
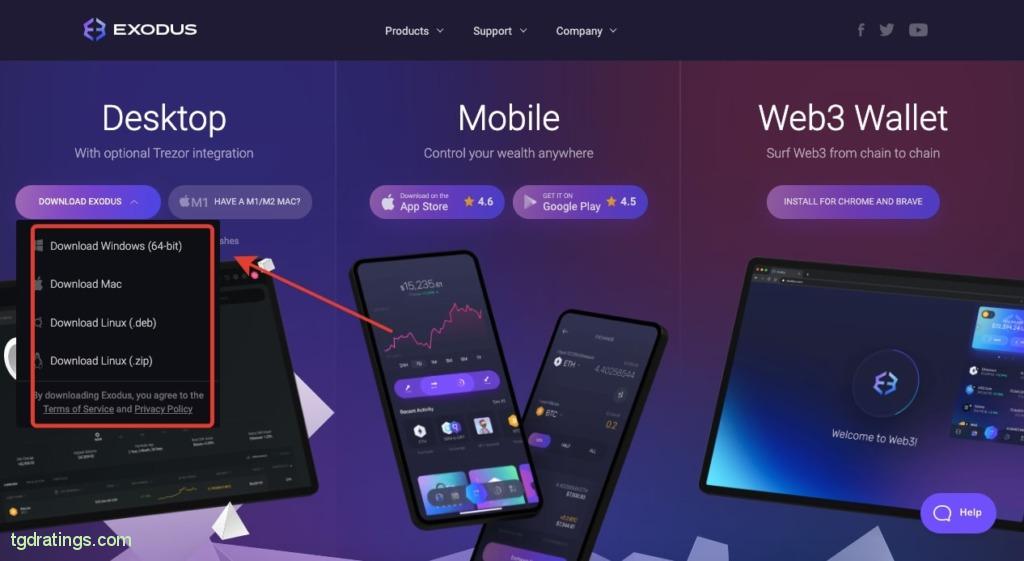
Exodus desktop wallet - Select the operating system you use;
OS selection - Install the wallet (about 1-2 minutes);
- After installing the wallet, the Exodus wallet icon will appear on the desktop of your OS.
Click on it: the program starts and the wallet will be ready to use.
Pros and cons
Online crypto wallets: pros and cons
Online wallet is a type of software (“hot”) wallet that is used in a browser and does not require installation on a PC. In fact, this is a website or browser extension where user can make cryptocurrency transactions.
However, the level of reliability of such storage is low. When using it, it is important to install additional wallet protection – enable two-factor authentication and anti-phishing encryption.
A guide to creating an online wallet
There is a step-by-step instruction for creating an online wallet using Guarda as example. Let’s check it out:
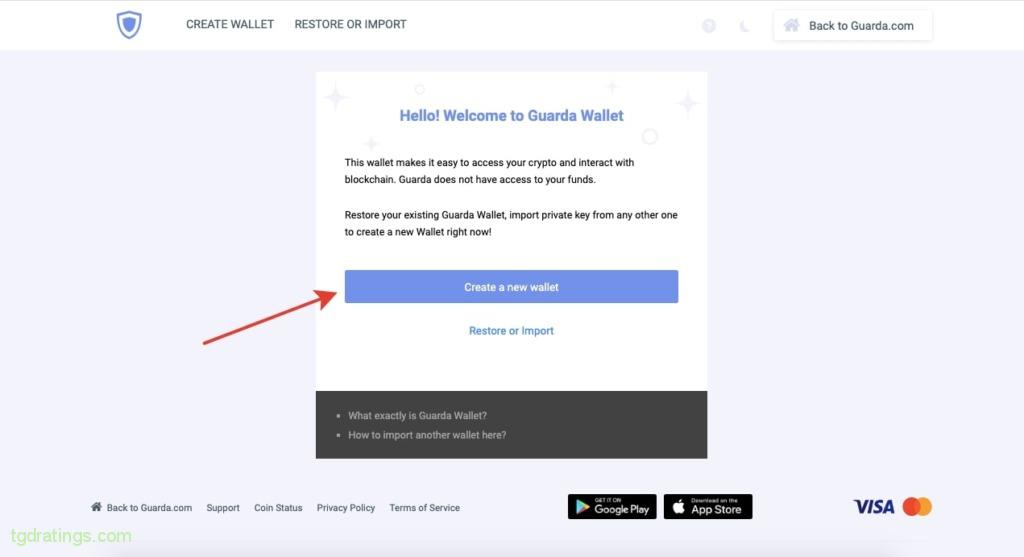
- Select Create Wallet on the official website;
Creating a Guarda wallet account - Click Create a new wallet;
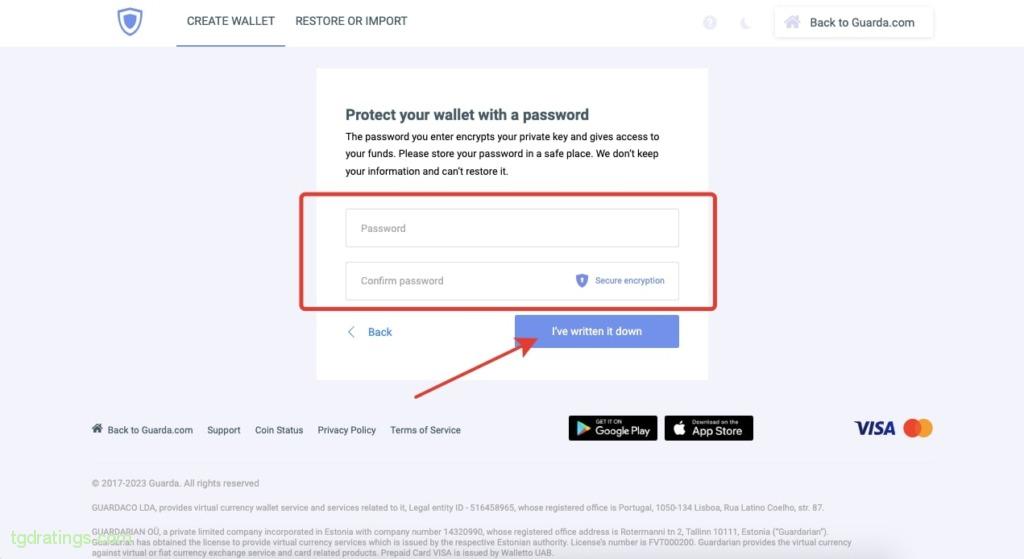
Creating a new wallet - Create a strong password and re-enter it. Be sure to write down and save the password in a safe place → click I’ve written it down;
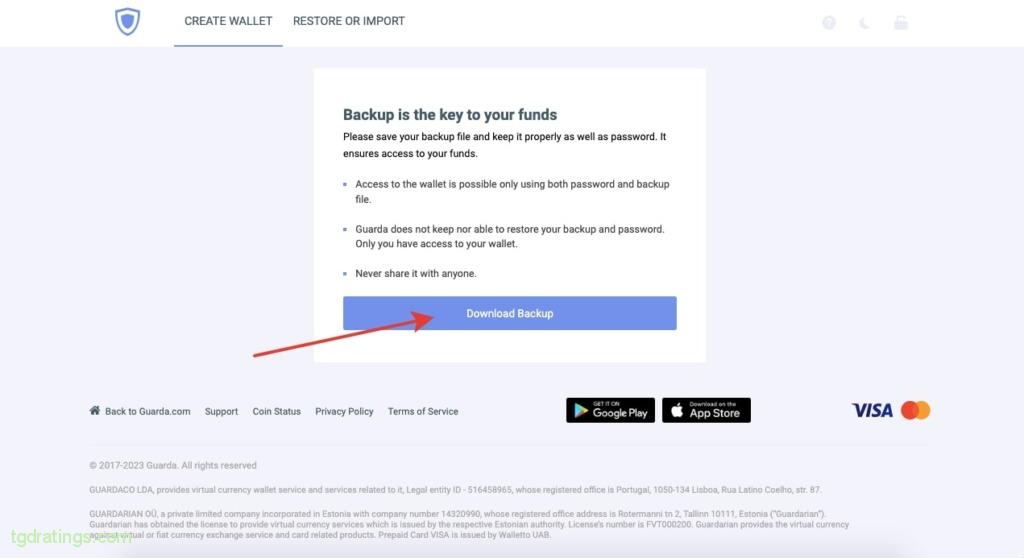
Password set up - Make the backup of the wallet by clicking Download Backup;
Loading a backup - The wallet is ready to use.
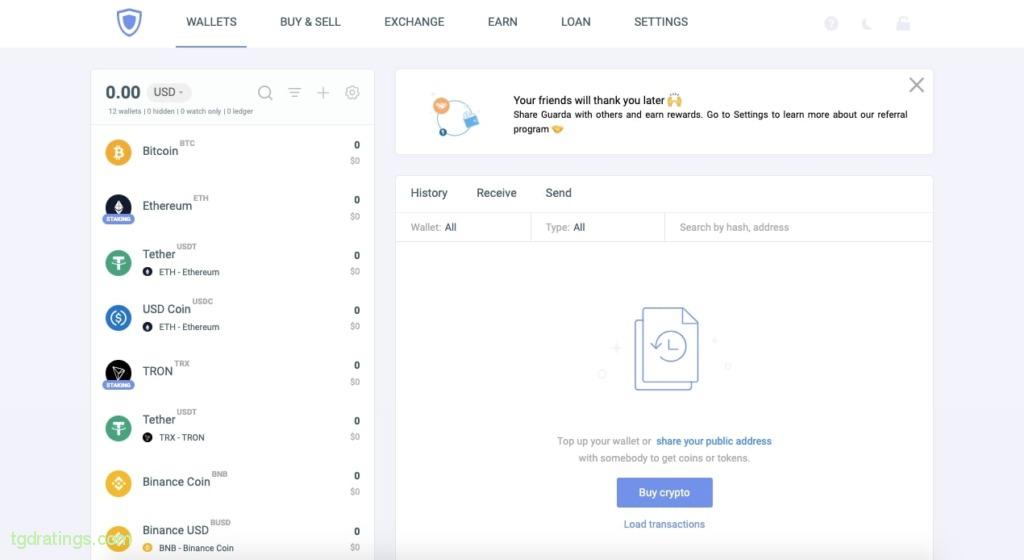
Guarda UI
Pros and cons
Mobile crypto wallets: pros and cons
Crypto wallet can be an application installed on a mobile device. Well suited for daily operations as they provide quick access to assets at any time.
Mobile wallets are easy to use and generally secure. When storing cryptocurrency in a mobile wallet, it is important to set up two-factor authentication, use a strong password, and create a backup.
Mobile wallet guide
Using Trust Wallet as an example, I will show you how to create a mobile wallet. The instruction is below:
- Download and install the Trust Wallet mobile app from the App Store or Google Play (depending on the software you use);
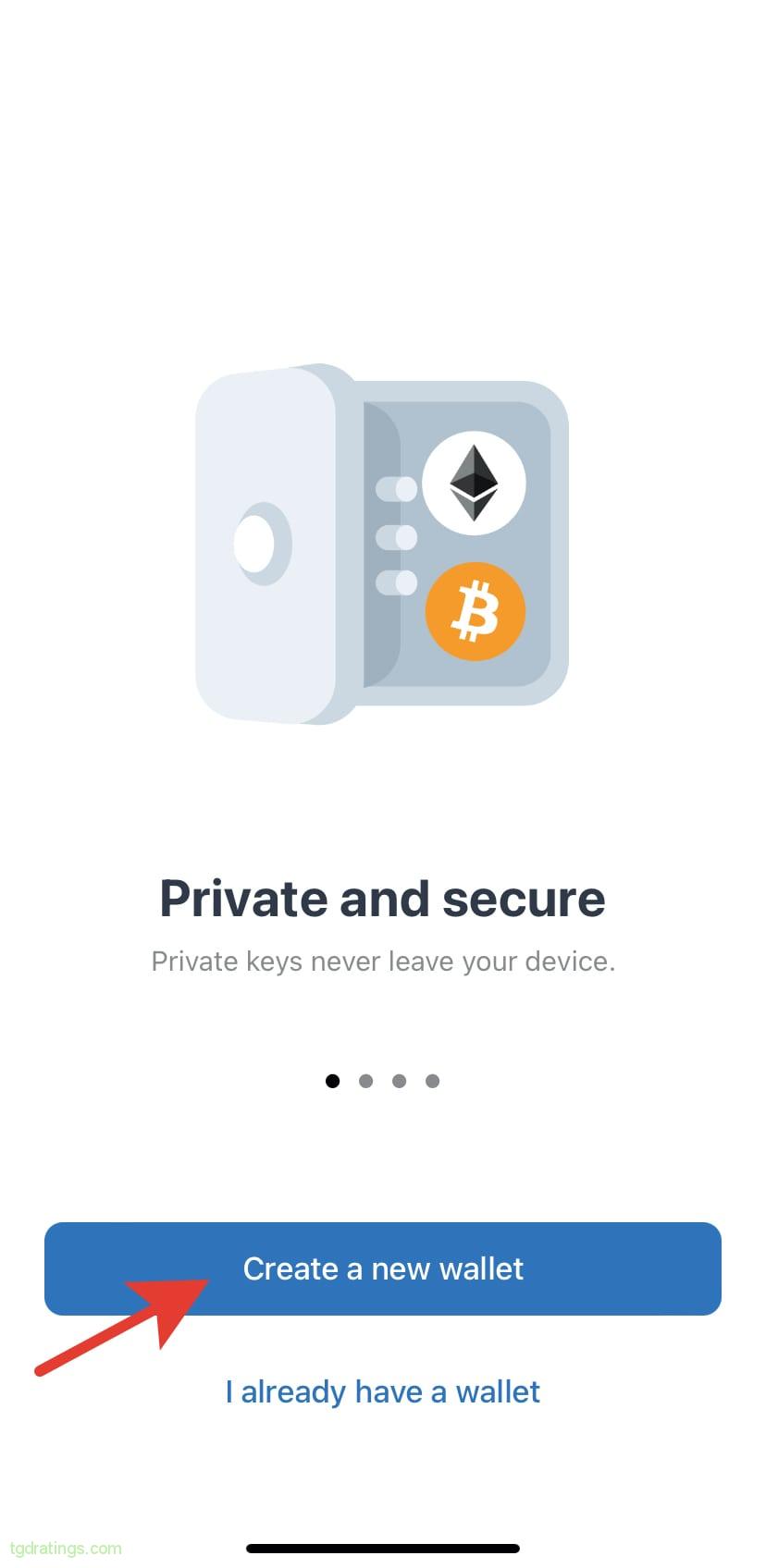
Trust Wallet on App Store - Open the application installed on your mobile device, select Create a new wallet;
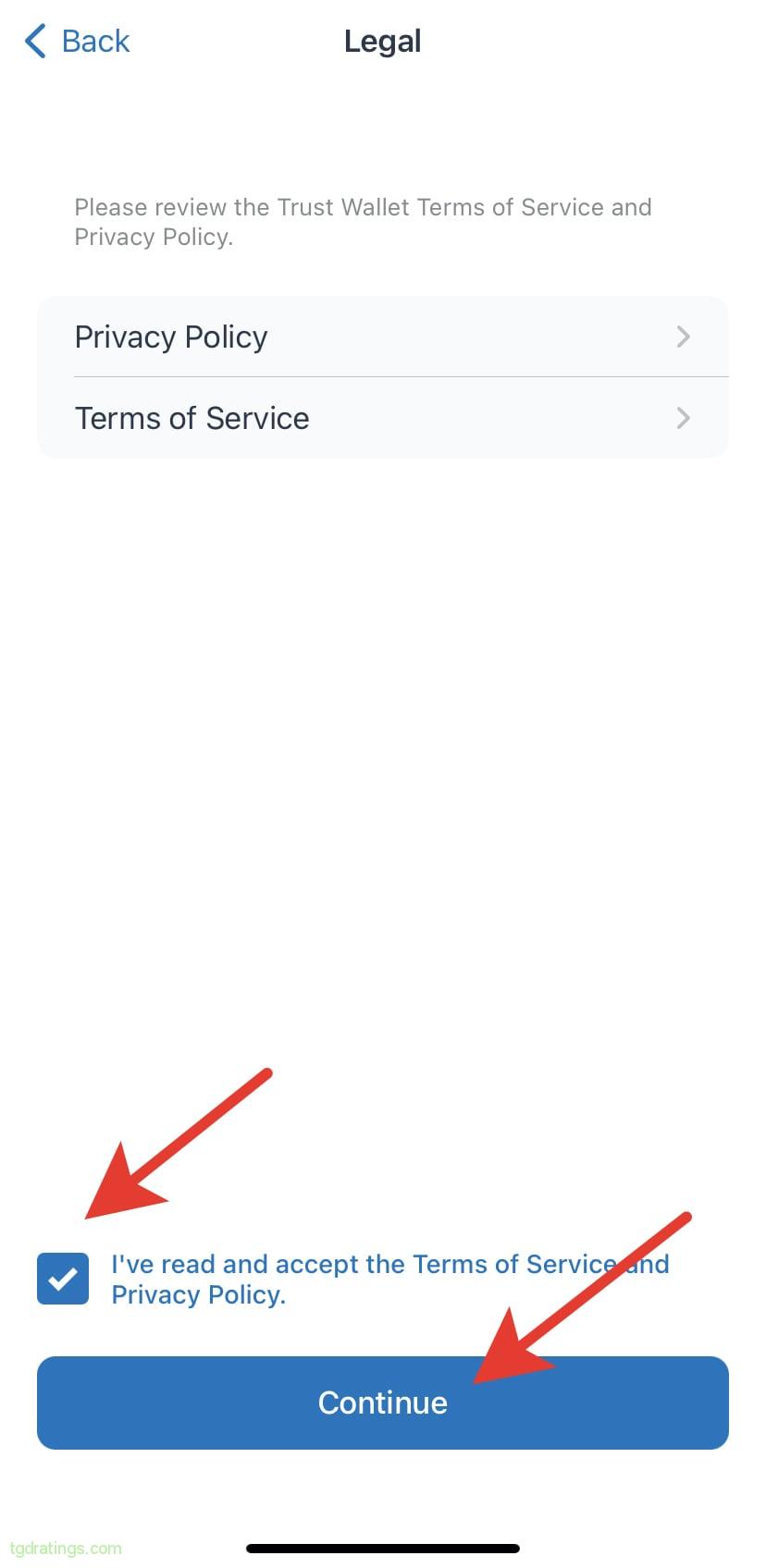
Create a Trust Wallet - Read and accept the terms of use of the service, check the box, click Continue;
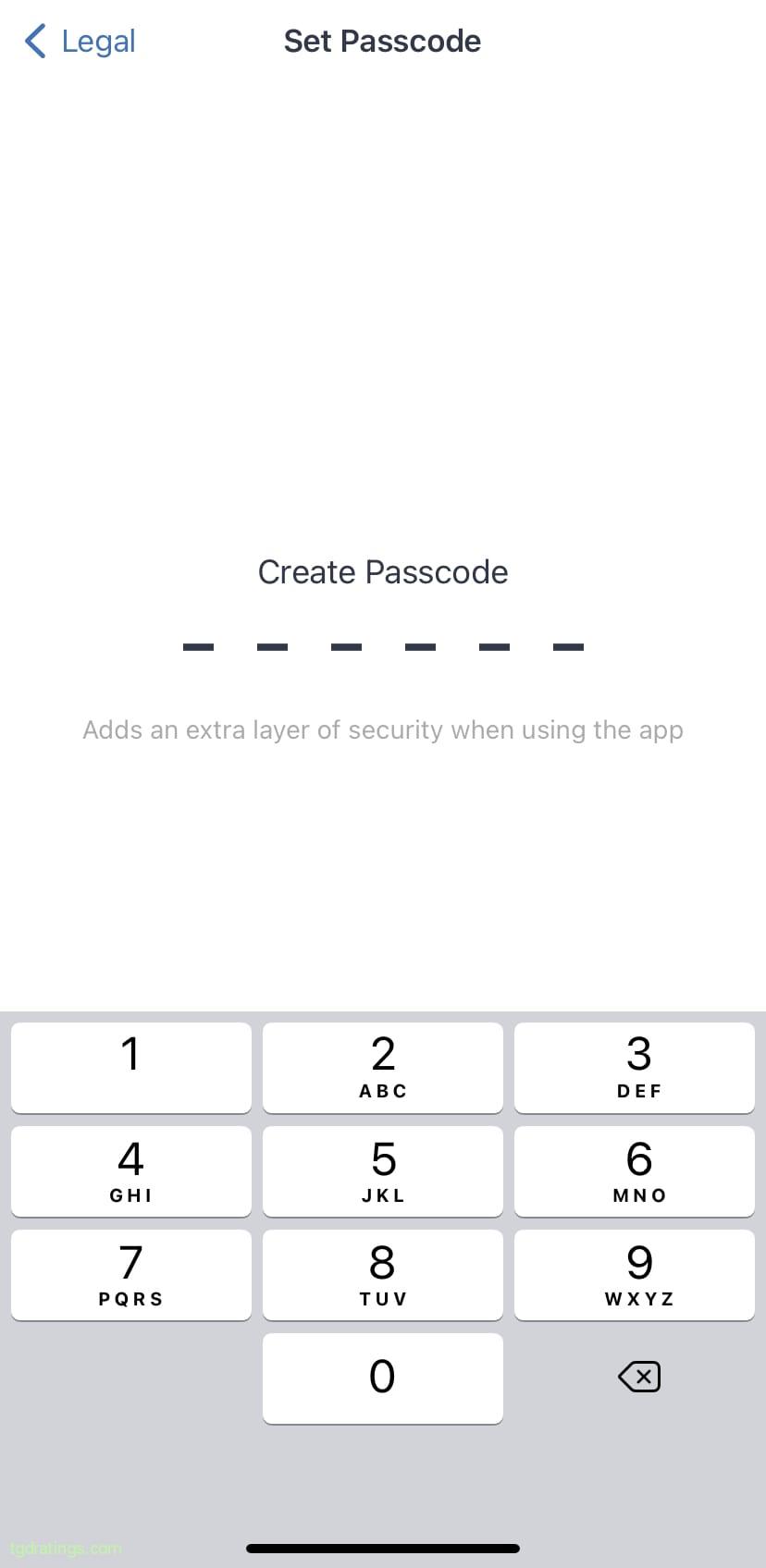
Trust Wallet terms of use - Create a 6-digit password and confirm it;
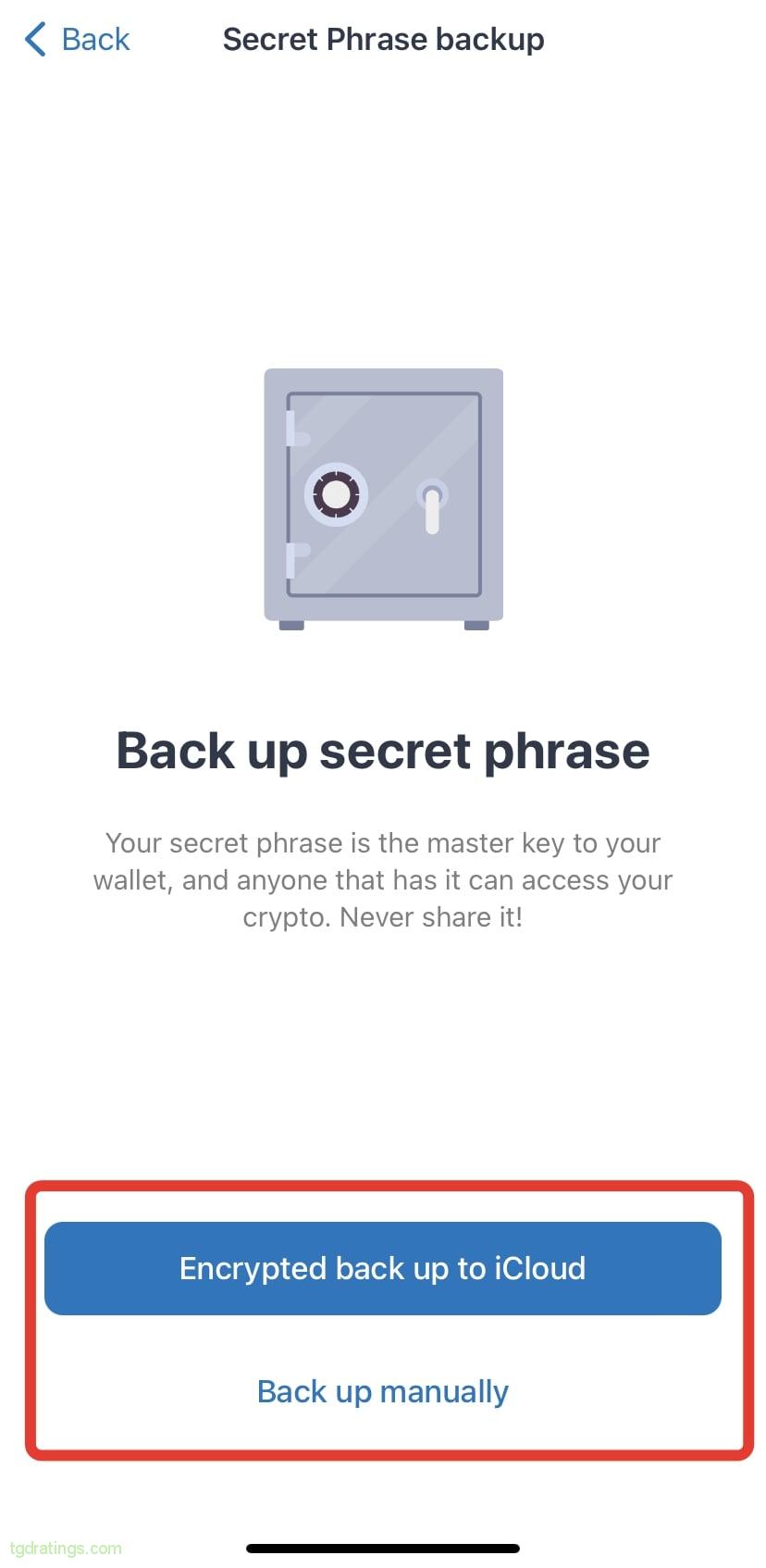
Password creation - Choose how you want to create a backup: using iCloud (Encrypted back up to iCloud) or manually (Back up manually);
Backup methods - When creating manually – read and accept the risks that the system will notify you of;
- After that, the screen will display the seed phrase in the form of a list of 12 words in strict order: write down and save the phrase in a safe place → Continue;
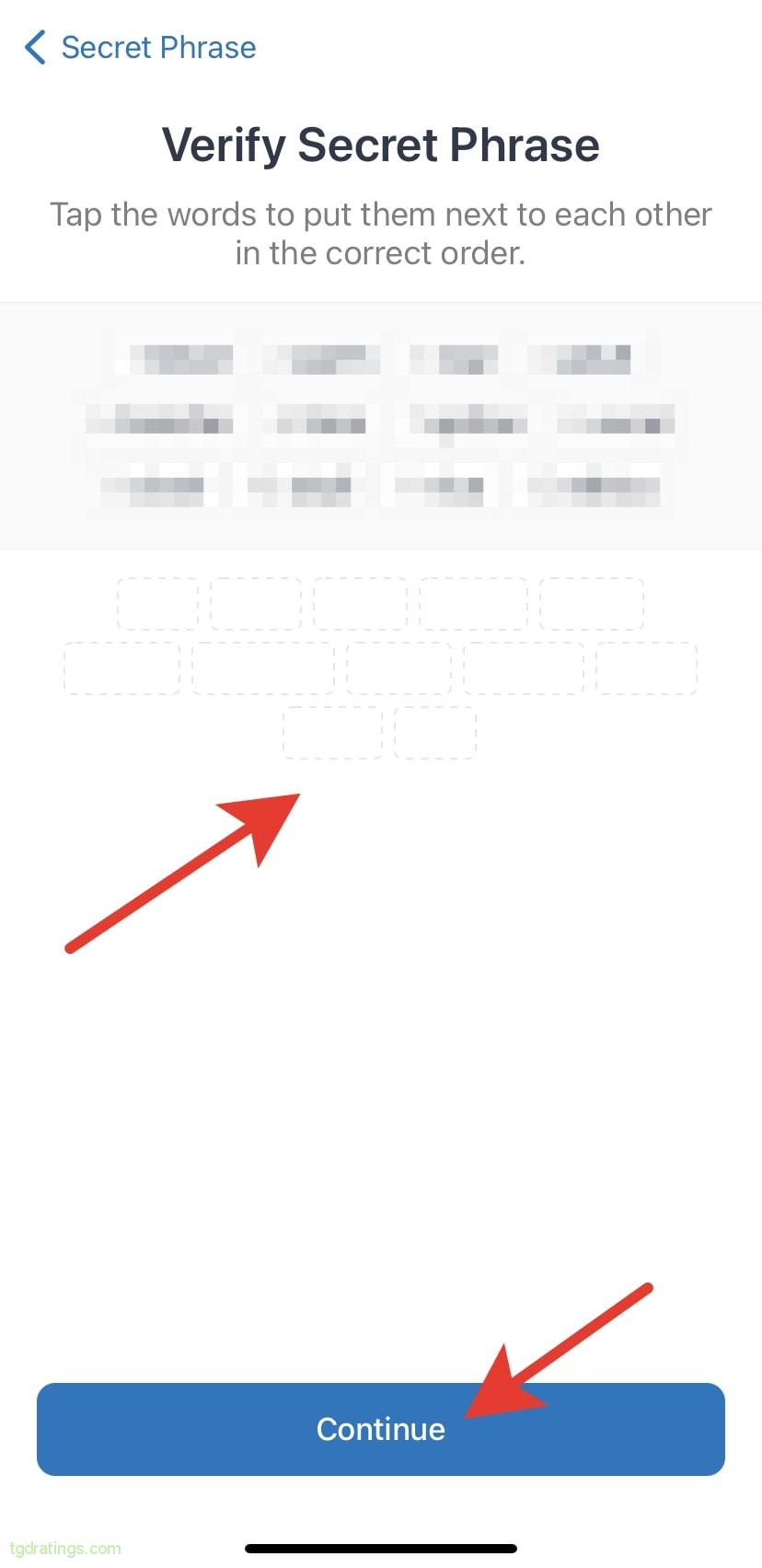
Secret phrase - Verify the recovery phrase by putting the 12 words in a proper order → Continue;
Verifying the seed-phrase - The wallet is ready to use.
Trust wallet UI
Pros and cons
Hardware crypto wallets: pros and cons
For long-term storage, as well as when it comes to large amounts of coins, it is most reliable to use a hardware (“cold”) wallet. It looks like a physical device often in a form of flash drive, which connects to the network only to make a transaction. Some hardware wallets have built-in Bluetooth and an option to generate QR-codes. At the moment, hardware wallets are the benchmark for secure storage of cryptocurrencies.
How to order a hardware wallet
For example, you want to buy Ledger hardware wallet. For this:
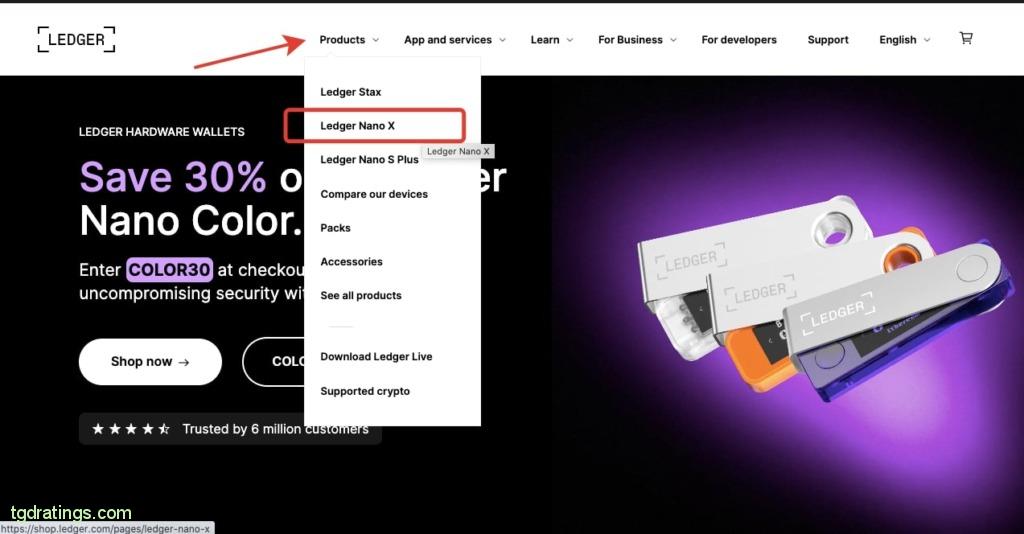
- Click the Products tab on the official Ledger website and select the specific wallet you want to order (e.g. Ledger Nano X);
Ledger wallets - To add the selected product to the cart, click Add to cart;
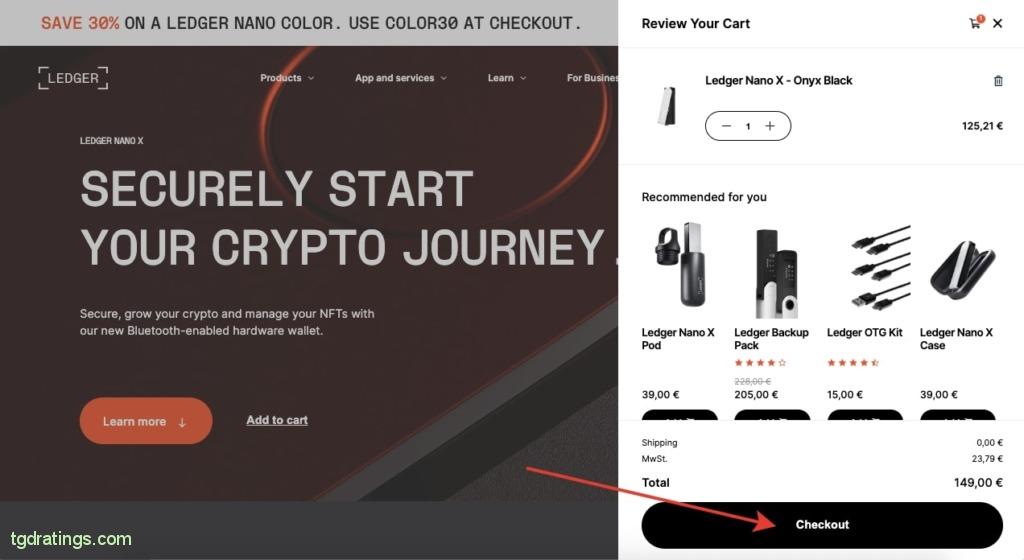
Add product to a cart - There will appear a pop-up window on the right side of screen, click Checkout;
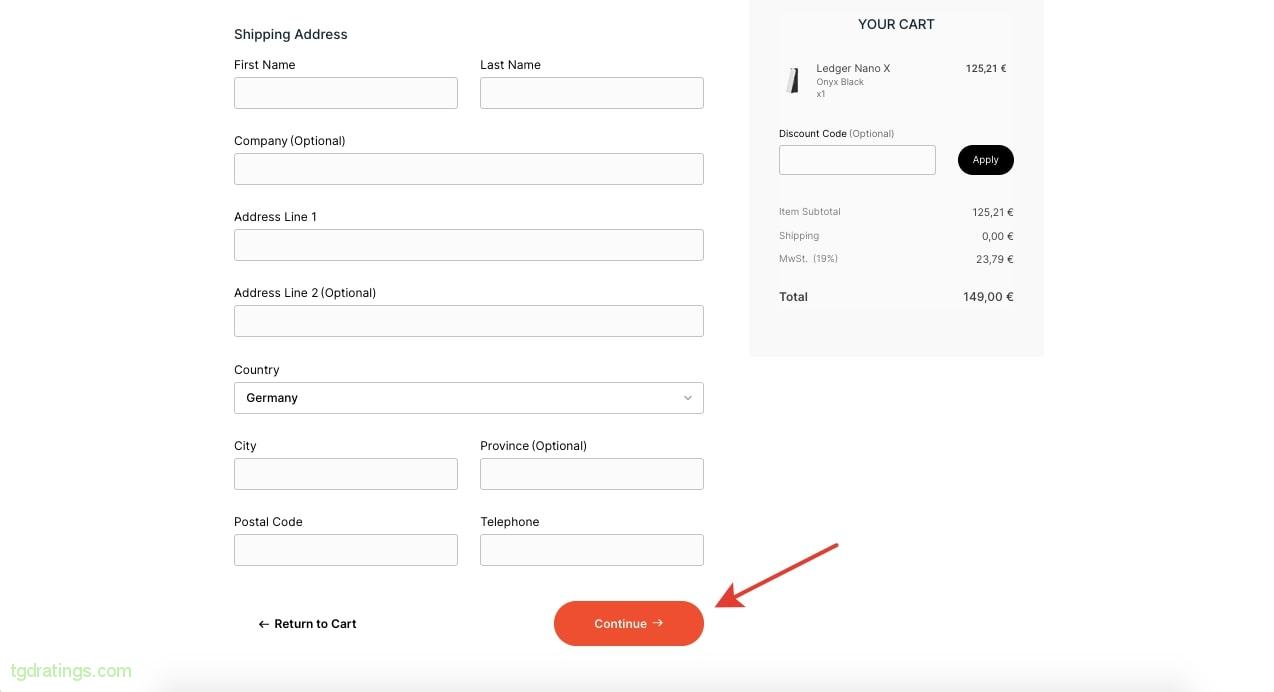
Verifying purchase - Enter email and shipping address → Continue;
User’s info - Specify the shipping method;
- Select a payment method (for example, Credit card) and enter payment details;
Purchasing with a card - Click Complete order.
Pros and cons
Top 5 cryptocurrency wallets in 2024
It is a list of 5 best wallets for cryptocurrency storing. There are different types of wallets in it – mobile, hardware, online, desktop and browser.
1. Trust Wallet
Address: https://trustwallet.com/
Trust Wallet is a mobile crypto wallet that provides a "hot" type of storage. Since 2018, it has been owned by one of the largest exchange – Binance.
- Foundation year: 2017;
- Supported blockchains and cryptocurrencies: 65+ blockchains and 4.5 million cryptocurrencies;
- Features: storage, sending, receiving, buying, assets exchange, staking, NFTs.
2. Ledger Nano X
Address: https://shop.ledger.com/products/ledger-nano-x
Ledger Nano X is a hardware wallet that provides a “cold” storage type. The device is equipped with a Bluetooth function and a USB-C cable. To store private keys and resist to hacking, the device uses certified Secure Element microcircuits.
- Foundation year: 2019;
- Supported blockchains and cryptocurrencies: 5000+ cryptocurrencies on the blockchains of Ethereum, BSC, Polygon, Tron, etc.
- Features: storage and management of crypto assets, purchase and instant swap, staking, NFTs, connection to mobile devices on iOS and Android.
3. Metamask
Address: https://metamask.io/
Metamask is a software “hot” crypto wallet presented as an extension for a browser and a mobile application. The service is used by 30+ million people worldwide.
- Foundation year: 2016;
- Supported blockchains and cryptocurrencies: Ethereum, Polygon, Binance Smart Chain, Avalanche, etc.;
- Features: storage, purchase, sending, receiving assets, swap function, access to decentralized applications (dApps), compatibility with Windows, Mac, Linux, iOS and Android.
4. Exodus
Address: https://www.exodus.com/
Exodus is a software wallet that comes in three types: mobile, desktop and browser extension. It is a non-custodial wallet and private keys are stored on the user’s device.
- Foundation year: 2015;
- Supported blockchains and cryptocurrencies: 50+ blockchains and 350+ cryptocurrencies;
- Features: store, buy, send, receive assets, buy cryptocurrency with USD, EUR and GBP using card, bank transfer, Apple Pay and Google Pay, staking, NFTs, Trezor hardware wallet compatibility.
5. Guarda
Address: https://guarda.com/

Guarda Wallet is a convenient multi-currency crypto wallet that provides high asset security. Can be used as a desktop, mobile and online wallet. The service does not store personal information, keys and other user data.
- Foundation year: 2017;
- Supported blockchains and cryptocurrencies: 50+ blockchains and 400K+ cryptocurrencies;
- Features: storage, purchase of 300+ assets, exchange, staking, crypto loans, Guard Visa Card cryptocurrency.
Crypto wallet security
When choosing a crypto wallet, make sure that it has the necessary security measures.
Use the following measures to protect your crypto wallet:
- Enable two-factor authentication;
- Update your software to the latest version;
- Back up your wallet regularly;
- Protect your seed phrase by storing it securely (multiple copies can be stored in different locations).
Crypto wallet recovering
As you know, the cryptocurrency is not stored in the wallet itself, but in the blockchain. Therefore, you can restore access to assets in case of losing your wallet using seed-phrase.
To restore access to private keys in case of loss of the wallet, you need to enter the seed phrase on any other device where the same wallet is installed.
FAQ
Conclusion
A crypto wallet is a service that stores the access to the records in the blockchain on coins you have. Access to this information is protected by two cryptographic keys: public (open) + private (secret).
There are different types of crypto wallets – desktop, browser, online, mobile, hardware. The first four from the list provide hot storage: they are constantly connected to the network and provide quick access to assets, but they are more susceptible to hacks. Hardware wallets offer cold storage of assets offline and have to be connected to the network only at a time of the transaction.
I considered at the pros and cons of each type of wallet, and also told how to create them. Much attention was paid also to the issue of restoring the wallet in case of loss/theft and the meaning of the recovery phrase for this process.


Comments (0)